Password Authenticated Connection Establishment (PACE) describes a password-based authentication and key agreement procedure that ensures that the contactless RF chip in ePassport or electronic ID card cannot be read without direct access and the data exchanged with the reading device is transmitted encrypted.
The PACE protocol was developed by the Federal Office for Information Security (BSI) for use in the new ID card and is used e.g. described in Technical Guideline TR-03110. PACE is standardized as the successor to Basic Access Control (BAC) for use in machine-readable travel documents (MRTD).
The protocol accepts a (possibly low – entropy ) password as input, verifies the password, and derives high-entropy session keys to protect subsequent communications.
PACE belongs to the family of Password Authenticated Key Exchange (PAKE) protocols. In contrast to other protocols of this group such as e.g. B. Encrypted Key Exchange (EKE), Simple Password Exponential Key Exchange (SPEKE) or Secure Remote Password Protocol (SRP), the PACE protocol itself is patent-free and can be implemented both with elliptic curves and with standard cryptography.
This protocol is used for the electronic ID card (eID).
Which password can be used for PACE depends on the digital certificate of the reading device. Usually this is the six digits secret “Personal Identification Number” (PIN), which is known only to the ID card bearer.
For reading devices with digital certificates for official use, such as boarder control, either the machine readable zone (MRZ) printed on the back of the electronic ID card or the six digits “Card Access Number” (CAN) printed on the front side is sufficient.
PACE has the advantage that the password length has no influence on the security level of the encryption. This means even with the short – in contrast to the MRZ – PIN or CAN the data is strongly protected on the RF chip of the electronic ID card and during transmission.
The PACE protocol consists of four steps:
- The chip chooses a random number (nonce), encrypts it using the password as a key and sends the encrypted random number to the terminal, which decrypts the random number again.
- The chip and terminal use a (possibly interactive) mapping function to map the random number to a generator of the mathematical group used.
- The chip and terminal perform a Diffie-Hellman key exchange using the generator from step 2 as a base.
- The chip and the terminal derive session keys from the shared secret and use them for mutual authentication and then to secure further communication.
One of the core components of PACE is a so-called mapping function. This function is used to map a random number into the mathematical group used for the asymmetric cryptosystem. Two types of mapping are currently defined:
- Generic mapping
- This mapping is based on generic group operations, is easy to implement and can be used with all Diffie-Hellman variants.
- Integrated mapping
- This figure integrates the random number directly into the group used. When used with elliptic curves, however, patented algorithms are required.
- Chip Authentication Mapping
- This mapping combines generic mapping with chip authentication so that both protocols can be run together, thereby increasing performance.
The safety of PACE is mathematically proven. The cryptographic strength of the session keys generated by PACE does not depend on the password used. Therefore, very short passwords can be used with PACE. As with all protocols from the group of password-based authentication methods, PACE cannot protect against brute force attacks on the password used. Possible countermeasures include slowing down the protocol or blocking the password after a set number of times the wrong password has been entered.
PACE is currently being standardized as the successor to Basic Access Control for use in machine-readable travel documents (MRTD) Due to the patenting of the integrated mapping for elliptic curves, this variant was declared as optional in the current version of the specification and is therefore not mandatory for readers.
In a transitional phase, PACE is initially to be implemented in parallel with Basic Access Control and is therefore also referred to as Supplemental Access Control for a transitional period . It is recommended that PACE be implemented in machine-readable travel documents and readers by 2015.
The new ID card uses PACE in conjunction with Extended Access Control (EAC) instead of Basic Access Control . Basic Access Control is no longer supported.
PACE can be run with 4 different passwords. The six-digit Card Access Number (CAN) printed on it and, analogous to Basic Access Control, the machine-readable zone are only approved for certain readers (usually from public authorities). A secret PIN and corresponding PUK , known only to the rightful owner, can be used with any reader. As the name suggests, the latter only serves to unlock the PIN after a certain number of failed authentication attempts.
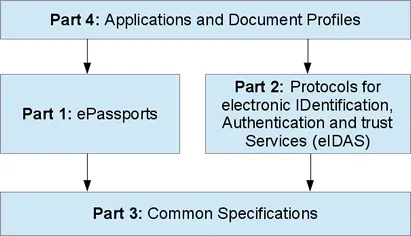
BSI TR-03110 Security Mechanisms Structure for MRTD and eIDAS Token
Related Products
Related Articles
Access-IS announce the OEM integration of its TripTick ticket reader and ATOM ADR300 document scanner with CCM’s Hybrid Self Service Bag-Drop counter
August 26, 2020 - Rather than choosing lines of either manned or unmanned counters, airport operators can configure the check-in hall according to the needs of that hour, day, week or even flight. The number of manned counters required increases
Access-IS enrolls with Acante
Reading, UK – June, 2020: Interactive kiosk design and manufacturing specialist Acante have announced the integration of the state-of-the-art Access-IS ATOM® document reader into their latest Biometric Enrolment Kiosk. 56 BEK01 kiosks and 75 desktop units have already been installed in the
Access-IS integrates with NOVOMATIC
READING, England - Access-IS, the leading provider of identity document readers, is pleased to announce the integration of its ATOM® document reader with the myACP casino management system from NOVOMATIC. The myACP modular system, combined with ATOM, can be
NXP Revolutionizes ID Security and Durability with World’s Thinnest Contactless Chip Module
EINDHOVEN, The Netherlands, Oct. 17, 2017 -- NXP Semiconductors N.V. (NASDAQ:NXPI) today announced its new, ultra-thin contactless chip module that transforms how passport and identity cards are designed. Measuring just 200 μm thick – roughly four times the thickness of
Panini Partners With Matica Technologies to Sell Financial Instant Issuance Solution
TORINO, Italy and DAYTON, Ohio, June 02, 2017 (GLOBE NEWSWIRE) -- Today, Panini, a global payments technology leader, announced the start of an exciting partnership with Matica Technologies to bring Financial Instant Issuance (FII) to the North American market. Panini has begun
Versasec, PrimeKey Formalize Working Relationship
Versasec, the leader in smart card management systems (CMS), and PrimeKey Solutions AB, a Swedish based world leading provider of advanced, open source public key infrastructure (PKI) solutions, announced today they have formalized their working relationship to benefit the



