- Built on Common Criteria EAL5+ Certified Silicon
- Powered by CardLogix’ M.O.S.T. Operating System
- High Capacity User Memory – Up to 144k Bytes EEPROM
- AES 256 and 3DES Encryption
- Special transport keys for lifecycle control
- SHA-256 HMAC for Mutual Authentication & eSignatures
- Extended file sizes that breaks the 32k byte barrier set by ISO
- Forensic information command
- Protocol: T=0
C7 – M.O.S.T. Card® Contact Microprocessor Smart Cards
Description
CardLogix M.O.S.T. Card® C7 Series is a contact microprocessor smart card family built on CC EAL5+ certified silicon and powered by the M.O.S.T. Card Operating System. The cards are designed for multi-function and/or high security applications. The C7 family features up to 144k bytes of user memory that can be configured for a wide variety of applications including national and civil IDs, driver licenses, voter IDs, patient IDs, single sign-on (SSO), multi-modal biometric credentials with secure messaging, and electronic healthcare records (EHR).
The M.O.S.T. C7 Card series features advanced password security logic, 3DES and AES 128-256 encryption, ICAO (BAC), SHA-256 and HMAC authentication, and e-Signatures with vaulted and threshold key protection for strong data integrity. Its 24 byte global unique identifier (GUID) makes the credential truly unique. The silicon provides continuous internal encryption of all data and the virtualization and rotation of the data across the non-volatile memory for secure data storage.
The M.O.S.T. OS also features an error detection code and security self-tests with built-in anti-tearing mechanisms to support heavy transactional environments. It supports a supports EF-level PIN/passwords as well as a Global Password with PIN-PUK & block/unblock features, multiple file types, and it includes an internal random number generator for unique transaction sessions.
CardLogix M.O.S.T. Toolz™ SDK lets you design a system that grows with your needs. M.O.S.T. Card is future-proofed while working on multiple silicon vendors’ devices, so your projects will always be supported. M.O.S.T. Cards enable multiple applications on a single smart card, and they are a mission critical component of the infrastructure to keep your system safe. Build confidence in your chain of trust with proven smart card technology and CardLogix services.
Specs
General Features
- Operating voltage range: 1.62V to 5.5V (ISO 7816 Class A, B, and C)
- CRC16 and CRC32 engines are compliant with ISO/IEC 3309
- Global unique card identifier system (GUID) is compliant with ASN.1 Object Identifier components (ITU-T Rec. X.667 | ISO/IEC 9834-8, and with IETF RFC 4122)
- Conforms to FIPS 197
- Authentication mechanisms are fully compliant to Secure Hash Standard (SHS) FIPS PUB 180-4
- Conforms to (HDLC) procedures ISO/IEC 13239:2002
- Programmable passwords for all access modes: read, write, update, invalidate and rehabilitate
- Data retention > 10 years
- Endurance: maximum of 16.5 million programming cycles at 25° C
- Electrostatic discharge protection > 6,000V
File Support
- Master File (MF)
- Directory File (DF)
- EF Transparent File
- EF Large File Size
- Linear, Cyclical, and Purse Files
- APP & CHV Password Files
- Master CHV File
- Admin Password with Injectable AES Keys
- Long File Name
Encryption/ Authentication
- SHA-1, SHA-256
- HMAC
- DES, 3DES
- AES-128, AES-192, AES-256
High-Security Architecture
- A wide variety of user memory sizes
- PC/SC compatible
- Negotiable communication speed (PTS)
- Rapid card development through M.O.S.T. Toolz™
- Multiple reader and terminal choices
- T= 0 or T= 1
- ISO 7816 1-4
Dedicated Semiconductor and Operating System Countermeasures Guard Against:
- Side channel attacks
- Advanced fault attacks
- Velocity checking
- Voltage attacks
- Frequency attacks
- Temperature glitch attacks
- Optical attacks
Custom Card Security Options
- Laser engraving/indenting
- Guilloche and rosettes
- Microprinting
- Optically Variable Devices (OVDs) and holograms
- Hidden Card Validator™ graphics with lens viewer
- Ultraviolet (UV) ink
- Watermark
- SBumps
Compare
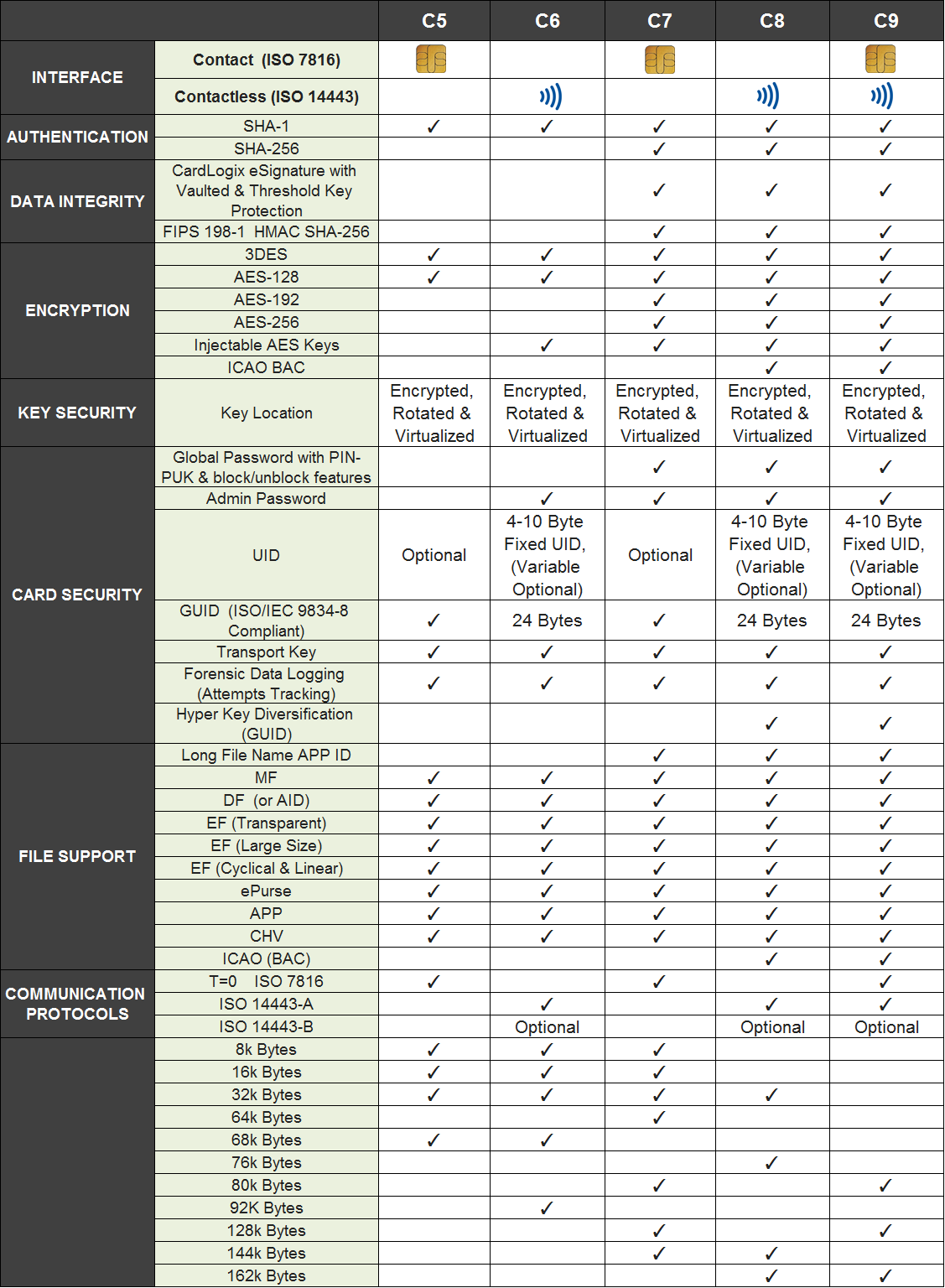
M.O.S.T. Card C Series | Features Comparison (C5, C6, C7, C8, C9)
Features
Advanced Security Features: SHA-256, HMAC and AES Encryption
The M.O.S.T. Card C7 is powered by CardLogix’ proprietary M.O.S.T Card Operating System which supports a variety of security measures, including SHA-1 bi-directional/ mutual authentication, SHA-256, HMAC, AES 128, AES 192, AES 256, 3DES (triple DES), APP and CHV PIN/passwords, and internal random number generation for unique e-signatures and transaction sessions. The OS is built with an error detection code and security self-tests. The EAL certified silicon provides continuous encryption of all data and the virtualization of the data across the non-volatile memory. The M.O.S.T. OS also features built-in anti-tearing mechanisms to support heavy transactional environments.
Up to 144k of EEPROM User Memory
The M.O.S.T. Card C7 family offers up to 144k bytes of user memory. The large EEPROM increases available user memory and card functionality, enabling the creation of advanced security files and multiple applications on one card. The C7 family allows a user to safely store and transmit a large amount of personal and sensitive data, including biometrics — data too vulnerable to manage over a loosely protected network. The M.O.S.T. Card C7 is capable of managing card holders’ and card issuers’ data on the card so that physical access controls systems, loyalty, e-payment and strong national ID, civil ID and in-the-field military identification systems can benefit from a secure, closed system that does not depend on being connected to a network at all times.
PKI Security Features at Affordable Symmetric Key Card Prices
The M.O.S.T. Card C7 leverages high security features typically found in Public Key Infrastructures (PKI), such as transport keys, AES encryption, and HMAC-SHA 256 for authentication and data integrity. PKI cards are priced, on average, 300% more than symmetric key cards. With the M.O.S.T. Card C7 series, you can get PKI security at the price of a symmetric key card, saving you money without sacrificing reliability and security. The Advanced Encryption Standard (AES) and HMAC-SHA 256 are the strongest encryption/ authentication algorithms to date. With the M.O.S.T. Card C7 series, your data will remain 100% confidential no matter where it is exchanged, and you will be able to reliably identify the source of and ensure the integrity of the message through randomly generated e-signatures. In addition, special transport keys ensure that data is secure across locations and along the card’s life cycle.
Injectable AES Keys with Admin Password — Ideal for Physical Access Control Systems
The M.O.S.T. C7 features an administration password with injectable AES keys that provide secure flexibility in applications that require password and system updates. With the M.O.S.T. Toolz™ Card Configuration Utility, the card issuer is able to create an administration password file, protected by a strong CHV password that cannot be accessed or changed once created. With the Admin Password File, an authorized security systems control manager can add injectable AES Keys if the door locks get changed or should any password modifications be needed. This allows the manager the scalability to safely update his or her physical access control system without having to re-issue cards.
Fast, Easy and Secure Smart Card Development
CardLogix has provided a complete line of user-friendly development tools to create both custom and pre-configured smart card applications. Project development for the M.O.S.T. Card C7 is supported by the PCSC API and the M.O.S.T. Toolz™ Card File Creation Utility SDK, including the powerful Winplex® API. The M.O.S.T. Toolz File Creation Utility features an intuitive user-interface that allows a card issuer the flexibility to design a M.O.S.T. Card file structure and set passwords that fit the needs of any custom smart card program. M.O.S.T. Toolz also provides intelligently constructed, pre-configured idblox™ applications, leveraging the M.O.S.T. Card Operating System. With this option, a card issuer’s only job is to set up passwords. Smart card development could not get any easier.
Eliminate the need to hire a graphic designer by starting with one of CardLogix’ professionally designed, pre-printed ReadyStart™ Secure Cards or Holofoil Cards, with embedded 2D holograms. Both use high security graphic printing technology that provides additional levels of physical security to your M.O.S.T. Card®
True Software and Hardware Interoperability
The M.O.S.T. Card C7 family is future-proofed, working on multiple silicon vendors’ devices so that your projects are always supported. The card family is part of the idblox™ ecosystem which has attracted multiple vendors for compatible smart card readers, smart card terminals, smart card applications and all other smart card infrastructure components.
Seamless Biometric Enrollment with Raven™ Biometric Enrollment Platform
CardLogix is strategically partnered with Corvus Integration, Inc., experts in biometric enrollment and biometric verification technologies, to bring you the simplest way to register personnel’s biometric information and load it onto a smart card within minutes. With Corvus’ Micro Booking Station, GIERS, PIK biometric enrollment and verification kits, biometric data is easily captured and transferred to The Card Encoding Engine™ for instant smart card encoding. A biometrically enhanced smart card provides the highest security and protection of personnel, data and valuable assets. With the M.O.S.T. Card C7, your organization can benefit from this level of security without having to spend more money than it’s worth.
Rapid Smart Card Personalization and Encoding — No Programming Required
The M.O.S.T. Card family is supported by the latest innovation in smart card personalization — The Card Encoding Engine™. The Card Encoding Engine is the first of its kind to offer smart card encoding without requiring programming in order to do so. This revolutionary software engine is the cornerstone of idblox™, allowing inline creation of a smart eID card program from design to use without relying on programmers, integrators or system designers.
Learn more about the idblox™ ecosystem, the only smart card ecosystem with true interoperability that enables the fastest, easiest and most affordable creation of high-security smart card programs for any card application.
Multiple Applications on One Card
With the M.O.S.T. Card C7, your organization can benefit from the economies of scale achieved by using one card for multiple purposes. Why settle for a single-purpose memory card when a company can combine a physical access control system (PACS), customer loyalty program, multi-factor identification, e-payment system, single sign-on, and player/ customer tracking onto one company-branded M.O.S.T. Card for the same price or less as a memory card? Improve your organization’s security by arming your employees with the M.O.S.T. Card to handle multi-factor authentication and non-refutable identification. Use the same card to control facility access rights, to institute an employee incentive program, and to protect classified or sensitive data. The application possibilities are endless, and the M.O.S.T. Card C7 can handle it all to meet any of your organization’s needs.
Development
M.O.S.T. Toolz™ SDK
Rated “Most comprehensive and professional SDK for smart card system developments”, MOST Toolz is designed for multi-function and high security smart card systems. M.O.S.T. Toolz™ is an affordable SDK and Card Configuration Utility for developing the M.O.S.T. Card® and other microprocessor smart cards. High level commands are sent through the Winplex® API to the card reader, which is included in the M.O.S.T. Toolz kit. M.O.S.T. Toolz enables programmers to create a smart card-based transaction system that updates and secures files while setting a variety of defensive measures to protect user ID, card access, and file information. CardLogix gives you the power to deliver multiple products and services on a single card, allowing for fast system design and easy updating without the need for card re-issuance.

MOST Smart Card Development
Applications
- Loyalty Cards
- Healthcare (EMR)
- Ticketing
- Cashless Vending
- Gaming
- Public Transit
- e-Banking
- Identity
- Charging the money card (e-purse)
- Enterprise Badging
- e-Passport personalization & verification
- PKI (public-key infrastructure) Applications
- e-Commerce (online payment)
- Secure network access
- Hospitality
- Electronic voting
- Computer security (log in access)
- Energy Management
- Border Crossing
- Customs
- Access Control System
- Time and attendance System
- Hazmat Cards
- Set-Top Cards
- Debit Cards, ATM Cards, Credit Cards
- Driving License
- Petrol Card
- National ID Cards
- NFC Payment
Definitions
- AES (Advanced Encryption Standard)
- A symmetric 128-bit block data encryption technique developed by Belgian cryptographers Joan Daemen and Vincent Rijmen. The U.S government adopted the algorithm as its encryption technique in October 2000, replacing the DES encryption it used. AES works at multiple network layers simultaneously. The National Institute of Standards and Technology (NIST) of the U.S. Department of Commerce selected the algorithm, called Rijndael (pronounced Rhine Dahl or Rain Doll), out of a group of five algorithms under consideration, including one called MARS from a large research team at IBM.
- Anti-tearing
- A card feature which protects the contents of memory if the card is removed before the end of the transaction.
- API (Application programming interface)
- A source code interface that a computer system or program library provides to support requests for services to be made of it by a computer program. An API differs from an application binary interface in that it is specified in terms of a programming language that can be compiled when an application is built, rather than an explicit low level description of how data is laid out in memory.
- CHV
- Cardholder Verification.
- DES (Data Encryption Standard)
- A widely-used method of data encryption using a private (secret) key that was judged so difficult to break by the U.S. government that it was restricted for exportation to other countries. There are 72,000,000,000,000,000 (72 quadrillion) or more possible encryption keys that can be used. For each given message, the key is chosen at random from among this enormous number of keys. Like other private key cryptographic methods, both the sender and the receiver must know and use the same private key.
- Electronic Health Record (EHR or EMR)
- An electronic health record is a collection of patient health information generated by one or more meetings in any care delivery setting. An EHR typically includes patient demographics, progress notes, problems, medications, vital signs, past medical history, immunizations, laboratory data and radiology reports. It’ss said to streamline clinicians’s workflow, and it has the ability to generate a complete record of a clinical patient encounter.
- E-purse (electronic purse)
- A smart card can be used to store a monetary value for small purchases. Card readers retrieve the amount currently stored, and subtract the amount for the goods or services being purchased. Groceries, transportation tickets, parking, laundromats, cafeterias, taxis and all types of vending machines are only some of the purchases that often do not reach amounts to justify the hassle of using a credit card (a cash card reader does not require a permanent phone connection with a host computer). Radio-read smart cards will allow the free flow of people through transportation systems, avoiding the need of ticketing machines or validation gates.
- FIPS (Federal Information Processing Standards)
- A set of standards that describe document processing, encryption algorithms and other information technology standards for use within non-military government agencies and by government contractors and vendors who work with the agencies.
- EEPROM
- A memory chip that can be reprogrammed any number of times, as to correct bugs, by first clearing its contents with ultraviolet light.
- GUID (Global Unique Identifier)
- A unique reference number used as an identifier in computer software. The term GUID typically refers to various implementations of the universally unique identifier (UUID) standard. A smart card can register support for an interface through association with the interface’s (GUID). This binding between a card and an interface is done at the time the card is first introduced to the system&emdash;typically when the SCSP is installed. Once the card is introduced to the system, applications can search for smart cards, based on a specific interface or GUID. For example, a cash card could make itself available to Windows-based applications by registering interfaces to access its purse scheme.
- HMAC
- HMAC stands for Hash-based MAC. It works by using an underlying hash function over a message and a key. Commonly used hash functions are MD5 and SHA-1. As computers become more and more powerful, increasingly complex hash functions will probably be used. Furthermore, there are several generations of SHA hashing functions (SHA-256, SHA-384, and SHA-512) which are currently available but not very widely used as their added security is not yet believed to be needed in everyday transactions.
- ISO (International Standardization Organization)
- An organization that sets standards in many businesses and technologies, including computing and communications.
- Microprocessor
- A chip that serves as the Central Processing Unit controlling a computer. It provides programmable intelligence.
- PC/SC (Personal Computer/Smart Card)
- A specification for smart-card integration into computing environments. Microsoft has implemented PC/SC in Microsoft Windows 200x/XP and makes it available under Microsoft Windows NT/9x. A free implementation of PC/SC, PC/SC Lite, is available for Linux and other Unixes; a forked version comes bundled with Mac OS X.
- PKI (Public key infrastructure)
- Enables users of a basically unsecure public network such as the Internet to securely and privately exchange data and money through the use of a public and a private cryptographic key pair that is obtained and shared through a trusted authority. The public key infrastructure provides for a digital certificate that can identify an individual or an organization and directory services that can store and, when necessary, revoke the certificates. Although the components of a PKI are generally understood, a number of different vendor approaches and services are emerging. Meanwhile, an Internet standard for PKI is being worked on.
- SHA-1 (Secure Hash Algorithm)
- A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm.
- SHA-256 (Secure Hash Algorithm)
- In cryptography, SHA-2 is a set of cryptographic hash functions in 224, 256, 384 or 512 bits designed by the National Security Agency (NSA) and published in 2001 by the NIST as a U.S. Federal Information Processing Standard.
- SDK (Software Development Kit)
- A package of pre-written code that developers can re-use in order to minimize the amount of unique code that they need to develop themselves. SDKs can help to prevent unnecessary duplication of effort in a development community.
- T=0
- A character-level transmission protocol, defined in ISO/IEC 7816-3. T=0 requires 2 request/response pairs per command (send command and get response saying got command, then a command to get the response and then the actual response).
- T=1
- A block-level transmission protocol, defined in ISO/IEC 7816-3. T=1 is newer than T=0. The block-oriented T=1 protocol is a half-duplex protocol and works with error detection (EDC) at the end of block.
- 3DES (Triple DES)
- Triple DES is a minor variation of this standard. It is three times slower than regular DES but can be billions of times more secure if used properly. Triple DES enjoys much wider use than DES because DES is so easy to break with today’s rapidly advancing technology. This just serves to illustrate that any organization with moderate resources can break through DES with very little effort these days.
Manufacturer
About CardLogix Corporation
Corporate Profile
CardLogix is an ISO 9001:2015 certified smart card manufacturer, software developer, and the premier provider of smart card technology with a comprehensive line of SDKs and tools that enable easy and rapid development of high quality smart cards. Since 1998, CardLogix has supplied millions of cards and card components to over 42 countries around the world. As an expert in smart card and chip technology, card operating systems, card software, development tools, and middleware, CardLogix has continuously been at the forefront of smart card technology.
CardLogix’ Mission
CardLogix’ mission is to make highly secure, high quality smart card systems more widely available to customers in need. CardLogix strives to make data transactions more secure, personnel and assets more protected, and to turn otherwise complex and expensive smart card systems into simpler, more cost-effective, and easier-to-develop solutions for everyone.
CardLogix Values
Trust is the primary commodity that CardLogix trades in every day. CardLogix builds and maintains customers’ confidence their products and processes, so that they can trust our cards to reliably protect personnel, sensitive data, and their most valuable assets. Starting with development software that’s flexible and easy to use to uncompromising customer support, CardLogix delivers on the promise of trust that our service inspires and our cards guarantee. Our company culture breeds initiative, commitment, and follow-through. As a global supplier and active industry participant, CardLogix understands the importance of being a responsible global business. With recycling, energy conservation, and full RoHS compliance, the company meets its goals with the environment in mind.
CardLogix Advantage
- Experts in smart card technology with an understanding of what it takes to get a card project from A to Z
- Commitment to ISO, ICAO, and industry conformance to ensure performance and interoperability
- Extensive partnerships with companies that offer complementary smart card infrastructure components
- Innovative products and solutions that simplify smart card development
- Cutting edge technology, sophistication and differentiated quality at a fraction of competitors’ costs
- Continuous customer support and involvement with evolving card projects
CardLogix Solutions
CardLogix manufactures high security and multi-functional ISO compliant smart cards, powered by CardLogix’ own operating systems. CardLogix offers easy-to-use SDKs for programmers, powerful middleware and APIs, a variety of applications software, and innovative solutions that empower end-users to develop and personalize smart cards without requiring any user-programming. The company partners with key suppliers in software, biometric capture, readers, and printers to deliver complete, leading-edge solutions. CardLogix smart card platforms provide solutions for multiple applications to markets globally, such as national, civil, voter and enterprise identity; physical and logical access cards; stored value; loyalty and rewards programs; e-purse; gaming, healthcare and other solutions that use a combination of multiple applications onto one card.