Features
Contactless Interface for Speed and Convenience
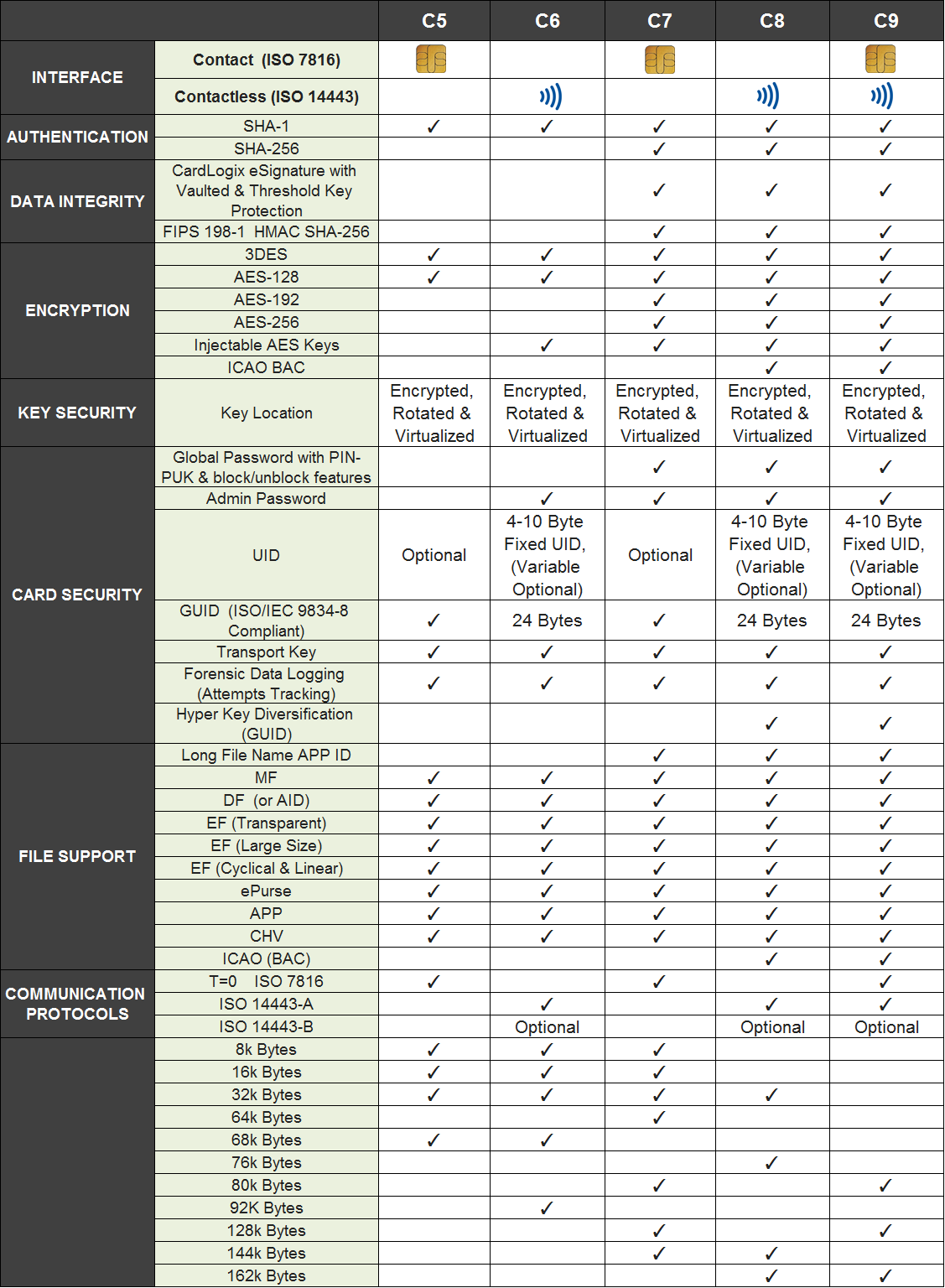
The M.O.S.T. Card C8 smart card features a contactless (RFID/ NFC) ISO 14443-A/B interface secured by an intelligent operating system and microprocessor (CPU) chip. Compared to low security/ low user memory contactless memory cards, such as MIFARE®, Prox® Card, and iClass®, the M.O.S.T. C8 contactless microprocessor smart cards are more reliable, more unique, and more secure— all while enabling the convenience and speed achieved by contactless communication.
Advanced Security Features — Including SHA-256, HMAC, and AES-256 Encryption
The M.O.S.T. Card C8 is powered by the CardLogix M.O.S.T Card Operating System which supports a variety of security measures, including SHA-1 bi-directional/ mutual authentication, SHA-256, HMAC, AES 128, AES 192, AES 256, and 3DES (triple DES). It also supports APP and CHV PIN/passwords with an internal random number generation for unique e-signatures and transaction sessions. The OS is built with an error detection code and security self-tests. The EAL certified silicon provides continuous encryption of all data and the virtualization of the data across the non-volatile memory.
Admin Password & Injectable AES Keys — Ideal for PACS Management
With the Admin Password File, an authorized security systems manager can inject new AES Keys if door locks are changed or if any password modifications are needed. This capability gives the manager the convenience to safely update his or her physical access control system without having to reissue the cards. The Admin Password File is created in the M.O.S.T. Card Configuration Utility™, and it is protected by a password that cannot be accessed or changed after setup.
True Credential ID Uniqueness
M.O.S.T. Card leverages the GUID (Globally Unique Identifier) serial number, proving a truly unique credential ID. The GUID is ISO/IEC 9834-8 compliant. With a length of 16 Bytes, ID number combinations have no chance of being duplicated or cloned. The UID, used in MIFARE and iClass cards, consists of only 6 bytes, and several duplicate ID numbers and cloned cards exist in the market today. The M.O.S.T. Card GUID enhances security while removing the need for identifier conflict resolutions.
Up to 144k of EEPROM User Memory
The M.O.S.T. C8 smart card family offers up to 144k bytes of user memory. The large EEPROM increases available user memory and card functionality, enabling the creation of advanced security files and multiple applications on one card. The C8 family enables users to safely store a large amount of personal and sensitive data, including ICAO-certified biometrics, in the smart card chip rather than over a vulnerable central network. The cards manage data securely, so that physical access controls systems, payment transactions, national ID, border crossing, and military identification systems benefit from a secure, closed system that does not depend on being connected to a network at all times.
Advanced E-Purse Security with Session Keys Every Command
M.O.S.T. Card C8 is built for reliable payment and ATM transactions. Unlike DESFire EV1, which generates a single session key when a card is inserted into a payment terminal, the M.O.S.T. Card C8 generates a new session key every time a new command is presented. Security attacks occur at any point from the time a card is inserted into the payment terminal to the time it is removed from the terminal. The M.O.S.T. Card C8 prevents these types of security attacks by generating session keys before every command while the card is still inserted into the terminal. Session keys performed this way conform to EMV (Europay, MasterCard and Visa) card payment security standards.
PKI Security Features at Affordable Symmetric Key Card Prices
The M.O.S.T. Card C8 leverages security features typically found in a Public Key Infrastructure (PKI), such as transport keys, AES encryption, HMAC, SHA 256 and e-signatures (SKI digital signatures) for trusted authentication and data integrity. PKI cards are priced, on average, 300% more than Symmetric Key cards. With the M.O.S.T. Card C8 series, the security of PKI is achieved at the price of a Symmetric Key card, saving your organization money without sacrificing reliability and security.
True Interoperability — idblox™ Certified
The M.O.S.T. Card C8 family is future-proofed, working on multiple silicon vendors’ devices so that projects are always supported. The card family is part of the idblox™ ecosystem which has attracted multiple vendors for compatible smart card readers, smart card terminals, smart card applications and all other smart card infrastructure components. The idblox ecosystem leverages a unique methodology that enables true card system interoperability without requiring programming for creating complete end-to-end ID card solutions.
Learn more about the idblox™ ID Credential Ecosystem, the only smart card ecosystem with true interoperability that enables the fastest, easiest and most affordable creation of high-security smart card programs for any card application.
Rapid M.O.S.T. Card Development
CardLogix provides a complete suite of user-friendly development tools to create both custom and pre-configured smart card applications for both programmers and users with average computer skills. Project development is supported by the powerful Winplex® API, demonstration programs, and the M.O.S.T. Card Configuration Utility™. The utility features an intuitive user-interface to design a M.O.S.T. Card file structure (CFS) and set passwords. It also includes pre-programmed, pre-configured idblox™ CFS templates that a user can select for a wide variety of identity applications. The kit includes a full set demo source code for C# (.NET framework), and for Java programmers we provide a set of introductory classes.
No-Programming Smart Card Personalization and Encoding
The M.O.S.T. Card family is supported by the newest innovation in smart card personalization, Card Encoding Engine™(CEE) ID Card Personalization Software. In addition to baseline design and printing capabilities, Card Encoding Engine is the only ID printer software capable of encoding smart cards without requiring programming, scripts, or custom APIs on desktop card printers. It also supports 1D/2D barcodes (including PDF417 and QR codes), MRTDs, and magnetic stripes. This revolutionary software solution is the cornerstone of the idblox ID Credential Ecosystem. It enables the inline creation and deployment of a smart card ID Credential program without relying on programmers, developers or systems integrators.
Streamlined Biometric Enrollment and Issuance
CardLogix is partnered with Corvus Integration, Inc., experts in biometric enrollment and biometric verification technologies, to bring the simplest and quickest way to enroll personnel’s biometric and biographic data and load it onto a smart card. The subject can be enrolled via a Corvus device or biometric enrollment station via Corvus RavenID™ software. The enrolled data is then seamlessly exported to Card Encoding Engine and then encoded and printed to the smart card. Biometric data stored within the smart card chip provides the highest security and protection of personal data and valuable assets.
Learn how RavenID™ software connects with Card Encoding Engine™ today to enable instant enrollment and issuance of a biometrics enhanced M.O.S.T. Card® ID Credential. Any company can interface to Card Encoding Engine by using our standardized idblox™ data dictionary with xml tags to build a rapid interface for ID production.
M.O.S.T. Toolz™ now supports on-card biometrics capability. For more information, see M.O.S.T. Toolz Biometric Series – Fingerprint Edition.
Options
M.O.S.T. Card C8 Contactless Microprocessor Smart Cards are available in the following sizes:
- CLXSU256KC8/T-CLED (32k Bytes)
- CLXSU608KC8/T-CLED (76k Bytes)
- CLXSU115MC8/T-CLED (144k Bytes)
- CLXSU129MC8/T=CLED (162k Bytes)
CardLogix Smart Cards are versatile and custom-made to meet Your Unique Requirements
CardLogix is a full-service card manufacturer. Cards are built from the inside-out, from card substrate selection and artwork preparation to chip initialization, personalization, and many other card options.
For a comprehensive list of our card offerings, see the CardLogix Smart Card Product Selection Guide
Custom Card Options
CardLogix can build the card that’s right for your application(s). Card options include a variety of card technologies, security graphics, custom design and printing services, and card substrates. All CardLogix cards can be developed as hybrid cards with both a contact and contactless interface. They can be combined with additional card technologies such as CPU or memory chips, magnetic stripes, 1D/2D barcodes, and MRZs (Machine Readable Zones). Combination cards and hybrid cards expand application possibilities for an infinite number of ID card solutions. This versatility also enables the integration of newer card technologies into legacy readers and systems to protect existing technology investment and lifespan.
Card Technologies
Hybrid Cards – Combination Cards
Add a memory chip or UHF chip/ tag to your smart card for legacy applications, such as payments for catering, vending machines, parking, or transportation; or for physical access systems. CardLogix can provide many chip options, including HID Prox® and 1125mhz proximity. These chips use RFID, NFC, and UHF technologies that follow the ISO/IEC 14443, ISO 15693, and ISO 18092 standards. Add a contact chip card, such as one of CardLogix M.O.S.T. Card® C5 or C7 microprocessor chips, for applications that require a secure contact interface. Combine with a M.O.S.T. Card C6 or C8 microprocessor chip for highest-security, high-speed, contactless applications.
Magnetic Stripe
CardLogix offers a full lineup of magnetic stripe card (magstripe) options. Magnetic Stripes are a useful feature to add to your cards so that they continue to work with existing legacy card readers and software programs. Magstripes are a good option for Loyalty Card programs or Gift Card programs. CardLogix can pre-load custom data on the magnetic stripe or it can be customer-encoded. The magnetic stripe card works in conjunction with the promoter’s software in order to provide the cardholder with special offers, credit toward purchases, and marketing incentives. It s also used in building databases that help analyze buying habits of customers. This information is useful because retailers can better serve their customer base by stocking the products they are most interested in buying. It also has many more uses that offer a wealth of valuable marketing applications.
Magnetic stripe options:
- 2trk & 3trk
- LoCo (300oe), MidCo (2750oe), or HiCo (4000oe)
- Stripe and card color options: black, white, gold, silver, red, brown, blue, green, and holographic
Barcode
CardLogix can print sequential or custom numbered barcodes using barcodes such as 2D, PDF417, 3 of 9, HIBC, code 128, etc. Barcoding is a popular option that can be added to any card. Most modern retail cash register systems read barcodes at the checkout stand so this is the perfect and fastest way to gather information about customers and to see what they are buying. It is also a great way to manage memberships in facilities and operations that have many cards to flow in and out. Each card is capable of carrying a unique barcode on either the front or reverse side. Another advantage of an ID card with a barcode printed on it is that it can be scanned extremely quickly to identify the user.
Primary Card Artwork: Design & Printing
The same background artwork that you see on every card for a specific program? That’s the primary card artwork. The background artwork gets printed and embedded at the point of card manufacturing. As card layers are stacked together, so is your artwork.
CardLogix offers graphic design, artwork preparation, and consulting services for your primary card artwork. Send what you have, and we’ll do the rest.
Secondary Card Printing
This is what gets printed after your cards are in their final shape. Secondary printing usually involves variable data; that is, data that is different on each card. This includes serial numbers, photo IDs, cardholder data, and more.
Depending on the size of your project, CardLogix can do this for you. Services include printing unique ID card numbers to each card, serialized laser engraving, and more. For smaller runs or for applications that involve distributed, instant card issuance, we recommend purchasing one or more ID Card Printers with ID Card Printer Software, such as CardLogix’ Card Encoding Engine
Custom Security Graphics
Security graphics are usually applied to cards at the point of manufacture. They use very specific, high-end printing and engraving technologies that make cloning and fraud extremely difficult for perpetrators.
Signature panel
Customers have the option of including a signature panel on the reverse of the card or a digitally scanned signature on the front of the card. Adding a signature panel to your card gives makes it possible to add information on the card at a later time.
Embossing and Tipping
Tipping refers to coloring tip of the raised or embossed letters with certain colors to make the numbers or letters stand out from the card. Gold and silver colors are available.
Sequential Numbering
This option can be added to any card order to help in the identification of a card holder or special program that the number may be referencing.
Laser Engraving
Add your company logo or symbol to your card to increase security or brand awareness. You can also laser engrave a unique or sequential number and/or barcode.
Additional Graphic Options:
- Full color offset printing
- Silk-screen printing
- Silver/Gold silk-screen printing background
- Variable Data Printing, such as numbers, photos, PIN codes and other information that is unique to each card
- Sequential Numbering
Additional Security Options:
- Laser engraving/indenting
- Guilloche and rosettes
- Microprinting
- Optically Variable Devices (OVDs) and holograms
- Hidden Card Validator™ graphics with lens viewer
- Ultraviolet (UV) ink
- Watermark
- SBumps
- Holographic lamination
Other Security Graphics Options:
- Numbering: Jet dot/ Thermal transfer/ Laser engrave
- Many flood colors are available
- Scratch Off Panels that reveal unique ID’s such as PIN number
- Variety of card thickness
- Plain and custom (such as company logo) Tyvek card sleeves
- Card wallet book such as for passports and themed books for promotional purposes
- Hole punch for ID clip necklaces
- SIM punch and key tag punched
- Card Surface: Matte/ gloss finish
Pre-Designed Security Graphics
These can be pre-printed on cards for purchases off-shelf, or they can be combined with other artwork.
CardLogix Holofoil Cards
CardLogix Holofoil Cards are a cost-effective and non-peelable alternative to holographic laminates for increasing a card’s physical security. The holofoils are embedded within the card substrate, providing a smooth surface with no damage to print heads. CardLogix Holofoil Cards can be purchased off-the-shelf with several designs to choose from, or they can be built to order with your custom designs.
CardLogix ReadyStart™ Secure Cards
ReadyStart Secure Cards are a family of pre-printed ultra-high resolution 2400 dpi security background plastic cards that enable a rapid start in the physical security, personalization and issuance of smart card and eID Credentials. ReadyStart Secure Cards are available off-the-shelf in many popular and industry-specific ID card designs. They significantly reduce the time and expense of custom graphic designing and card printing. Corresponding ReadyStart background templates can be found in CardLogix Card Encoding Engine™ Card Personalization software.
Card Substrate Options
CardLogix’ standard card is constructed with white, commercial grade PVC substrate and a mirror-mirror finish for use with desktop printers. Other, higher-end card substrates are available.
Commercial Grade Cards
Commercial Grade Cards are general purpose card bodies for applications such as loyalty and libraries. The majority of PVC cards in your wallet today are made with Commercial Grade substrates, and they are the most cost effective option.
PVC (Polyvinyl chloride)
PVC is the most widely used material for plastic cards, and has been used for photo IDs for more than 10 years. Low in cost, the smooth surface of photo quality PVC material accepts dyes for high quality ID image printing and is compatible with most laminate materials.
PET (Polyethylene terephthalate)
PET is a polyester material that was used for many years for the punch laminate style of IDs. It is a crystalline plastic and has higher heat resistance than PVC. Durable and resistant to moisture and chemical attack, the material is typically used as an outer laminate for PVC, composite and Teslin cards. PET is more expensive than PVC, and is generally used as part of a multi-part card construction.
Biodegradable Grade Cards
These eco-friendly, biodegradable cards are manufactured from corn and based on the (NatureWorks® PLA) material. They look and feel identical to traditional plastic PVC cards.
Precision Identity Grade Cards
Precision Identity Grade Cards should be used when dimensional tolerances are critical and when the cards will be printed with additional graphic imaging (such as an employee badge).
Government Certified Cards
Government Certified Cards are uniquely built to meet ongoing card body certifications and requirements for different governments. CardLogix can help you come through with the toughest cards certified today.
Molded ABS SIM Cards
Molded ABS SIM Cards are designed for the specific demands of the Telecommunication industry. These cards have a higher Vicat softening point, and are best suited for the high temperatures in mobile devices and are rarely handled by the consumer.
PC (Polycarbonate)
Polycarbonate is an extremely durable thermoplastic polymer resistant to high temperatures and impact. Used in items like DVDs and CDs, it is receptive to offset security printing. PC is not compatible with variable printing, such as resin transfer or dye diffusion. When constructed with a very thin transparent laser receptive layer, PC cards can be laser engraved with very high definition graphics. Cards can be assembled with RFID, IC and contactless technology. PC is more difficult to manufacture, and is more expensive to produce than PVC or composite cards. PC cards are primarily used with laser technology to produce black images/text. PC or PC composite cards are typically used for the longest life and/or highest security IDs.
Applications
M.O.S.T. Card® C8 Contactless Microprocessor Smart Cards feature AES encryption, SHA-256 authentication with e-signatures, injectable AES keys, an Administration Password, and up to 144k Bytes of user memory. M.O.ST. Cards contain a microprocessor (CPU) chip providing multifunctionality. Combination and Hybrid card options further extend application capabilities. The cards can be configured for a wide variety of applications, including ID-1 ICAO Border Crossing Cards, Access Control (PACS), Single Sign-On (SSO), Healthcare IDs, Voter IDs, transportation payments, contactless badging with on-card storage of biometrics, and applications that require a contactless session key purse function. The card works with all standard Android NFC devices. for applications that give users immediate access to information stored on the card. For more infomation, view this short demo video.
Applications Include
- Physical access control systems (PACS)
- Transportation passes
- Border crossing cards (ID-1 ICAO cards)
- E-Payment with E-Purse functionality
- Logical access control and single sign-on (SSO)
- Identity verification and mutual card authentication
- On-card biometric storage for identity verification
- Loyalty and rewards programs
- Player tracking
- TITO replacement
- Time and attendance tracking
- Multiple applications on one card
Physical Access and Logical Access ID Cards
- Room keys
- Building entrance
- High security vault access
- Password replacement for network and/or computer access
- Secure transfer of data
- eDriver licenses
- Mass transit fare collection systems
- Electronic toll collection systems
- Bus fares
- Parking fees
ID Cards for Government and Enterprises—Identification and Physical and Logical Access Control Systems
- Driver license
- Voter ID
- Civil ID
- Military ID
- National ID
- Visitor ID / Alien ID
- Worker ID
- Employee ID
- Physical access control systems (PACS)
- Logical access and single sign-on (SSO)
Government Programs
- Electronic benefits for food stamps and WIC food benefits to replace paper coupons and vouchers
- Agricultural producer smart marketing card to track quotas
- eSocial Card
- eVehicle Registration Card / eCar registration
- Multi-functional ID cards for staff and patients
- Patient records (EHR or EMR) – Electronic Health Records Management
- Equipment and room access control
- Patient ID, doctor ID, staff ID
- Prescription card with drug dosage information
- Hospital admission card
- Consumer health card with insurance eligibility and emergency medical data
- Embedded solutions for medical equipment
- Frequent use card for hemodialysis, chemotherapy, or other treatment medical devices
Player’s Card: Player Tracking, TITO Replacement, Physical Access, and Secure Online Gaming — All on One Card!
- Hotel room keys
- Loyalty and rewards programs
- E-payment for restaurants and shopping
- TITO replacement
- Player tracking and rewards
- Multi-factor authentication for online gaming
- Biometric authentication for offline and online use providing a card present transaction
School Campuses
Multi-Application ID Cards for Room Access, Meal Plans, Time & Attendance, Test Taking, and More
- Student identification
- Teacher identification
- Staff identification
- Visitor identification
- Time and attendance
- Test taking
- Library cards
- Meal plans and school merchandise purchase
Financial Applications
- Electronic purse to replace coins for small purchases in vending machines and over-the-counter transactions
- Stored value for pre-paid payment cards
- Credit and/or debit accounts, replicating what is currently on the magnetic stripe bank card, but in a more secure environment
- Authentication of EDI transactions that combats fraud
- Internet commerce authentication device for securing payment across the Internet
- Micropayment
- Billing management and the secure initiation of calls and identification of caller on any GSM (Global System for Mobile Communications) or CDMA (Code Division Multiple Access) phone
- Pre-paid telephone cards
- Subscriber activation of programming on Pay-TV
- Consumer reward and redemption tracking (frequent shopper or frequent flyer) on a smart loyalty card, marketed to specific consumer profiles and linked to one or more specific retailers serving that profile set
- Loyalty and E-purse applications
Manufacturer
Corporate Profile
CardLogix is an ISO 9001:2008 certified smart card manufacturer, software developer, and the premier provider of smart card and biometric technology with a comprehensive line of software development platforms and applications that enable easy and rapid development of high quality smart cards and ID systems. Since 1998, CardLogix has supplied millions of cards and card components to over 42 countries around the world. As an expert in smart card and chip technology, card operating systems, card software, development tools, and middleware, and biometrics, CardLogix has continuously been at the forefront of smart card technology. Strong partnerships with key suppliers in software, biometric capture, readers, and printers enables CardLogix to deliver complete, leading-edge solutions for multiple applications to markets globally, such as national, civil, voter and enterprise identity; physical and logical access cards; stored value; loyalty and rewards programs; e-purse; gaming, healthcare and other solutions that use a combination of multiple applications onto one card.
CardLogix’ Values
Trust is the primary commodity that CardLogix trades in every day. CardLogix builds and maintains customers’ confidence in our products and processes, so that they can trust our cards and software to reliably protect personnel, sensitive data, and their most valuable assets. From development software that’s flexible and easy to use to uncompromising customer support, CardLogix delivers on the promise of trust that our services inspire and our cards guarantee. Our company culture breeds initiative, commitment, and follow-through. As a global supplier and active industry participant, CardLogix understands the importance of being a responsible global business. With recycling, energy conservation, and full RoHS compliance, the company meets its goals with the environment in mind.
CardLogix’ Mission
CardLogix’ mission is to make high security and multifunctional ID Credential systems more widely available for organizations in need. CardLogix strives to make data transactions more secure, personnel and assets more protected, sensitive data more private, and to turn otherwise complex and expensive smart card system projects into streamlined, easier-to-develop, and more cost-effective solutions for both integrators and end-users.
CardLogix Advantage
- Experts in smart card technology with a deep understanding of what is involved to get a smart card project from A to Z
- Commitment to ISO, ICAO, and industry conformance to ensure performance and interoperability
- Extensive partnerships with companies that offer complementary smart card infrastructure components
- Innovative products and solutions that simplify smart card development
- Cutting edge technology, sophistication and differentiated quality at a fraction of competitors’ costs
- Continuous customer support and involvement with evolving card projects
CardLogix manufactures high security and multi-functional ISO compliant smart cards, powered by CardLogix’ own operating systems. CardLogix offers easy-to-use software development platforms for programmers, powerful middleware and APIs, a variety of applications software, and innovative solutions that empower both integrators and end-users to develop and personalize smart cards with less dependency on programming.